Published On: September 16, 2025

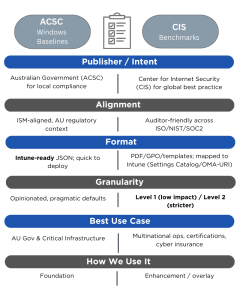
Bottom line: ACSC ensures local compliance; CIS adds global credibility.
How we implement (quickly):
1. Import ACSC Windows baseline JSON into Intune.
2. Roll out in rings (Pilot → Broad → All).
3. Resolve conflicts and track drift via Intune reports.
How we layer on top of ACSC:
1. Map CIS items in Intune (Settings Catalog / OMA-URI).
2. Apply Level 1 org-wide; reserve Level 2 for privileged or high-risk devices.
3. Document justified deviations and monitor with Intune + Defender insights.
1. Start with ACSC as the non-negotiable foundation (compliance and speed via Intune).
2. Overlay CIS for breadth and auditability (L1 everywhere; L2 where risk demands).
3. Operate monthly: update baseline versions, review exceptions, verify control effectiveness, and reconcile drift.
1. Start with Microsoft Security Baselines — Deploy Windows, Edge, and Defender baselines as your secure default.
2. Overlay CIS Benchmarks — Add CIS Level 1 org-wide; use Level 2 only for sensitive or privileged devices.
3. Operate Monthly — Monitor compliance and drift, update baselines in pilot first, and validate with Defender for Endpoint.
We can deliver a pilot in days—import ACSC, layer CIS, resolve policy conflicts, set up ringed deployment, and build a monthly governance rhythm (reports, exceptions, version updates).
👉 Book a Windows Hardening review and assessment
👉 Talk to Our Security Experts
Australia
P: +61 3 9087 8057 E: info@cloudpoints.com.auSingapore
P: +65 6990 7890 E: info@cloudpoints.com.sg